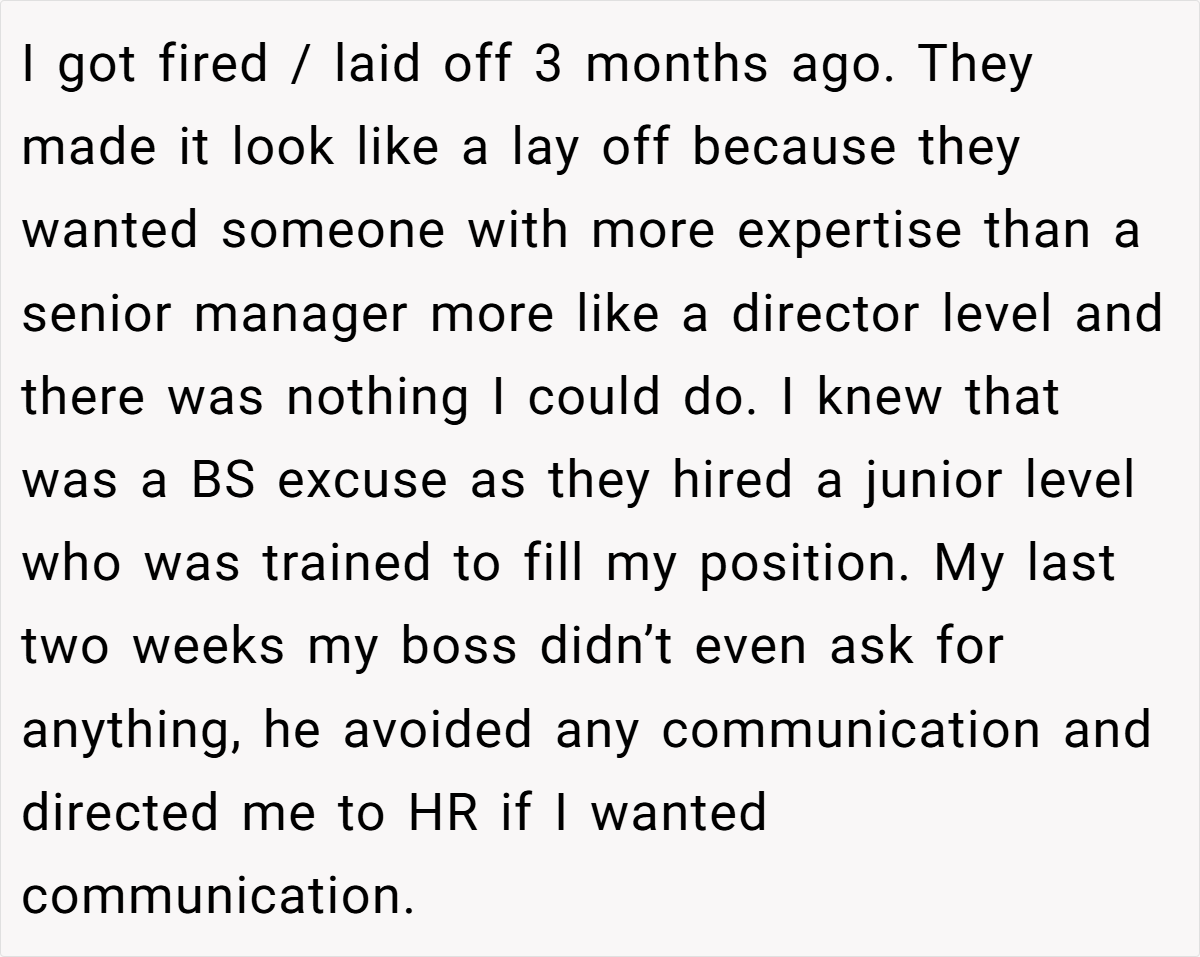
AITA if I don’t provide the code my boss needs after they fired me?
Navigating the aftermath of a layoff can be challenging enough without having to worry about lingering digital entanglements. In this story, a recently fired senior manager finds himself caught between his former employer’s expectations and his own sense of fairness.
After being let go under questionable pretenses—and seeing the company hire someone less experienced in his stead—he’s now faced with an unusual request: his old boss is trying to use his personal phone for two-step verification to log into a work account.
This situation not only highlights the often messy handover process after termination but also raises an important question about boundaries in professional relationships. Is it fair to be expected to facilitate access to a system long after you’ve been shown the door? Let’s dig into the details and see how experts and the community weigh in on this modern workplace dilemma.
‘AITA if I don’t provide the code my boss needs after they fired me?’
Workplace boundary expert Dr. Karen Miller emphasizes that “once an employee is terminated, the formal obligations between employer and employee are meant to cease immediately.” She explains that offboarding procedures exist for precisely this reason—to prevent any post-employment entanglements that might compromise either party. “If your employer fails to execute a proper exit process, it’s a clear indicator of their internal disorganization.
The responsibility to retrieve access, change passwords, and transfer system ownership lies solely with them. Relying on an ex-employee’s personal device or cooperation is not only unprofessional, it creates significant security risks,” she adds. Cybersecurity consultant Jason Rivera expands on these concerns by highlighting the dangers of linking corporate systems to personal devices.
“When a company uses personal phones for two-factor authentication, they blur the boundaries between corporate security and personal privacy. This practice is inherently flawed, particularly when an employee is no longer with the organization. It not only exposes sensitive data to potential breaches but also places an unfair burden on the former employee, who has no further obligation to assist,” Rivera states.
He suggests that companies should invest in proper IT infrastructure that relies solely on company-issued hardware to avoid such complications. Adding another layer, HR specialist Angela Ruiz underscores the importance of a robust offboarding process. “A well-structured offboarding process should include a comprehensive handover of responsibilities and immediate revocation of all access rights.
If you’re being contacted for a verification code three months after your departure, it’s a sign that the company’s procedures have failed. It’s not your responsibility to cover the gaps in their process,” she explains. Ruiz notes that when organizations neglect these protocols, they not only jeopardize their operational integrity but also risk legal complications by involving ex-employees in ongoing work-related security measures.
Together, these experts agree that the responsibility for managing and securing work-related systems remains with the company after termination. While it might be tempting to assist, the ex-employee is under no obligation to facilitate access or support the company’s internal transitions.
Instead, companies should be held accountable for their offboarding failures and take full responsibility for any ensuing issues. In essence, the decision to withhold the verification code is not only justified but also a necessary act of professional boundary-setting.
Let’s dive into the reactions from Reddit:
The Reddit community has largely sided with the ex-employee. Many commenters remarked that the company’s failure to conduct a proper exit process meant that the responsibility to assist now falls on them—not him. Users emphasized that he should not be held accountable for his former employer’s poor planning, with one user even calling the situation “a prime example of how not to handle offboarding.”
The overall sentiment was clear: if his boss needs access, they should have arranged for it before terminating his employment, not three months later using his personal phone for two-factor authentication.
Ultimately, this incident raises an important question about where professional responsibilities end. Is it fair to expect a former employee to facilitate access to systems after their departure, especially when proper offboarding procedures were never followed?
The consensus among experts and community members is that the company should bear the burden of resolving these technical issues. What do you think? Have you ever faced a similar situation in your workplace? Share your thoughts and experiences on where the line should be drawn between post-employment support and personal boundaries.